Open Threat Intelligence
The Open Threat Intelligence integration represents a collection of publicly available resources that specify whether certain entities are malicious or not. Categories of entities include IPv4 addresses, domains, URLs, file names, and hostnames.
Currently this integration uses resources published by the following vendors:
Arcanna - Open Threat Intelligence
By integrating with Open Threat Intelligence, Arcanna.ai enriches security events. This helps the decision-making process make a more informed decision about a certain event by adding more context to it. As a result the information provided by Open Threat Intelligence should be added before the process makes the decision.
Each vendor can be individually activated or deactivated when used in an Arcanna.ai use case.
Steps to configure Open Threat Intelligence
Prerequisites
- A valid Arcanna.ai instance - for setup, follow this user guide.
- (Optional): An AlienVault OTX API Key if you plan on using this vendor. The other vendors don't use any authentication method.
How to obtain an AlienVault API Key
- Register on AlienVault Go to your AlienVault Dashboard, click the
API Integrationtab - Copy the DirectConnect API Key from the right panel:

How to connect
Go to the Arcanna.ai instance:
-
Create an OpenThreatIntel integration
- Go to the Integrations tab
- Search for the OpenThreatIntel integration and click on it
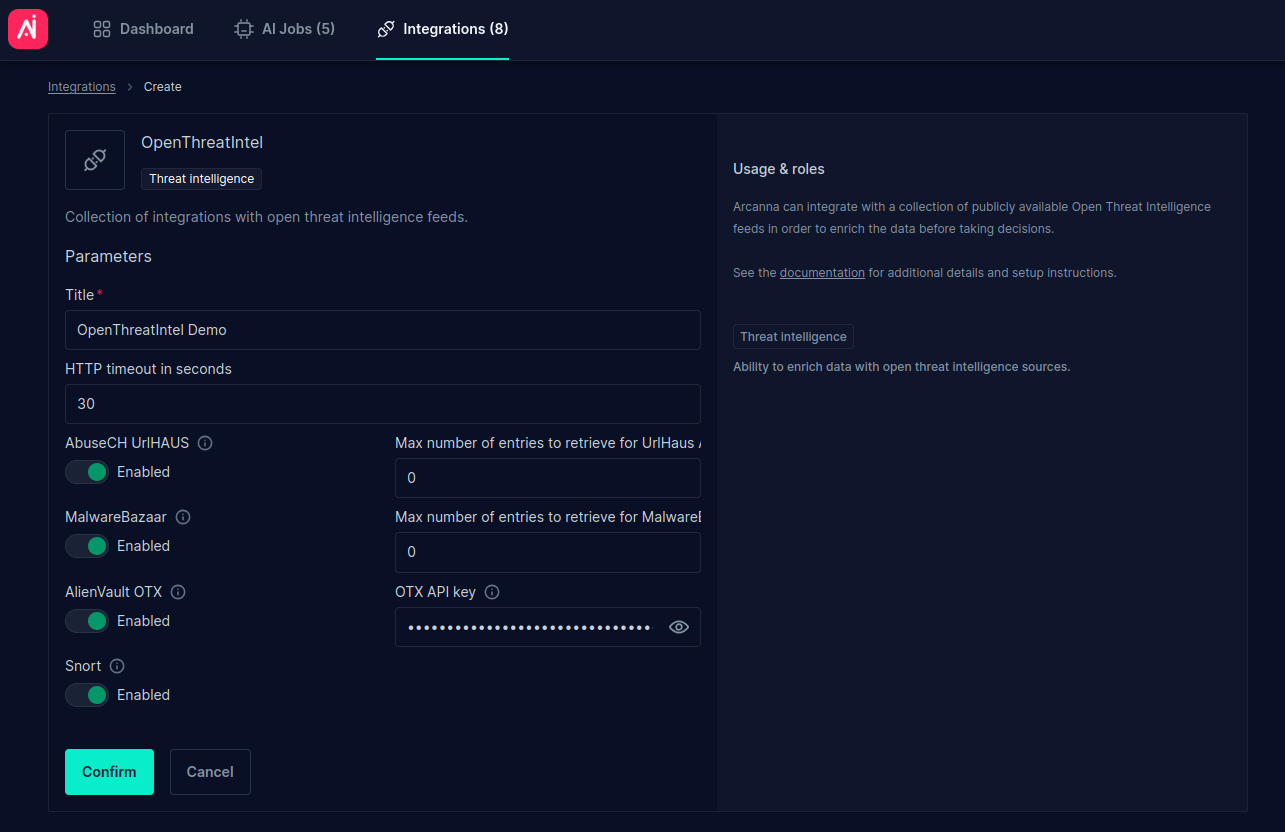
- Type your Title. Enable each vendor as you see fit. If you decided to use AlienVault OTX pass the API key from the AlienVault dashdboard.
 |
| -
Create and Arcanna.ai use case using the Open Threat Intelligence integration:
- Go to AI Use Cases tab and click Create Use Case
- Complete the Title and select an input integration. For testing, we can use an Elasticsearch input integration and an index that contains IP resources in one of its fields. The name of the index in this case is:
openti-demo-index
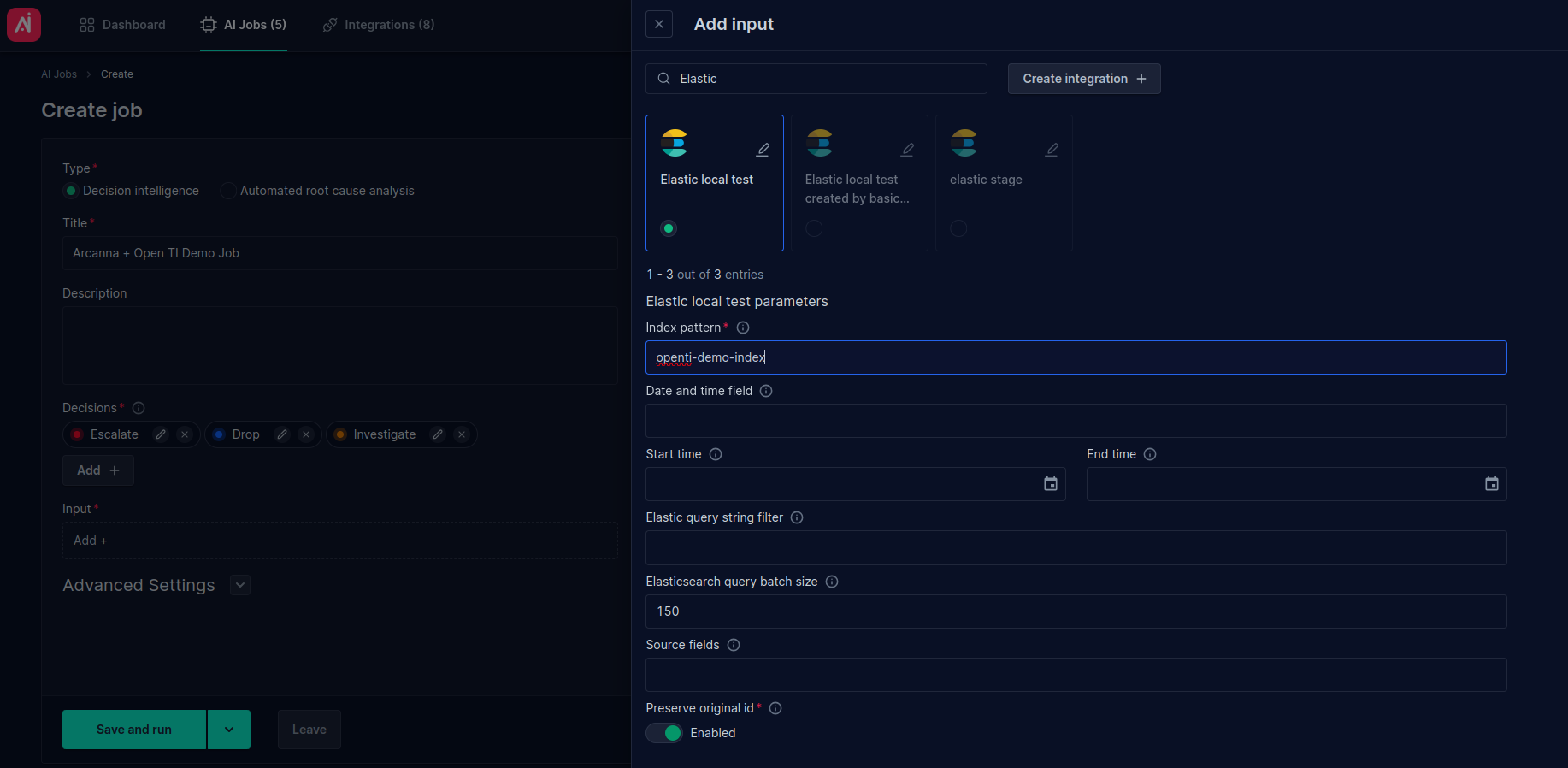
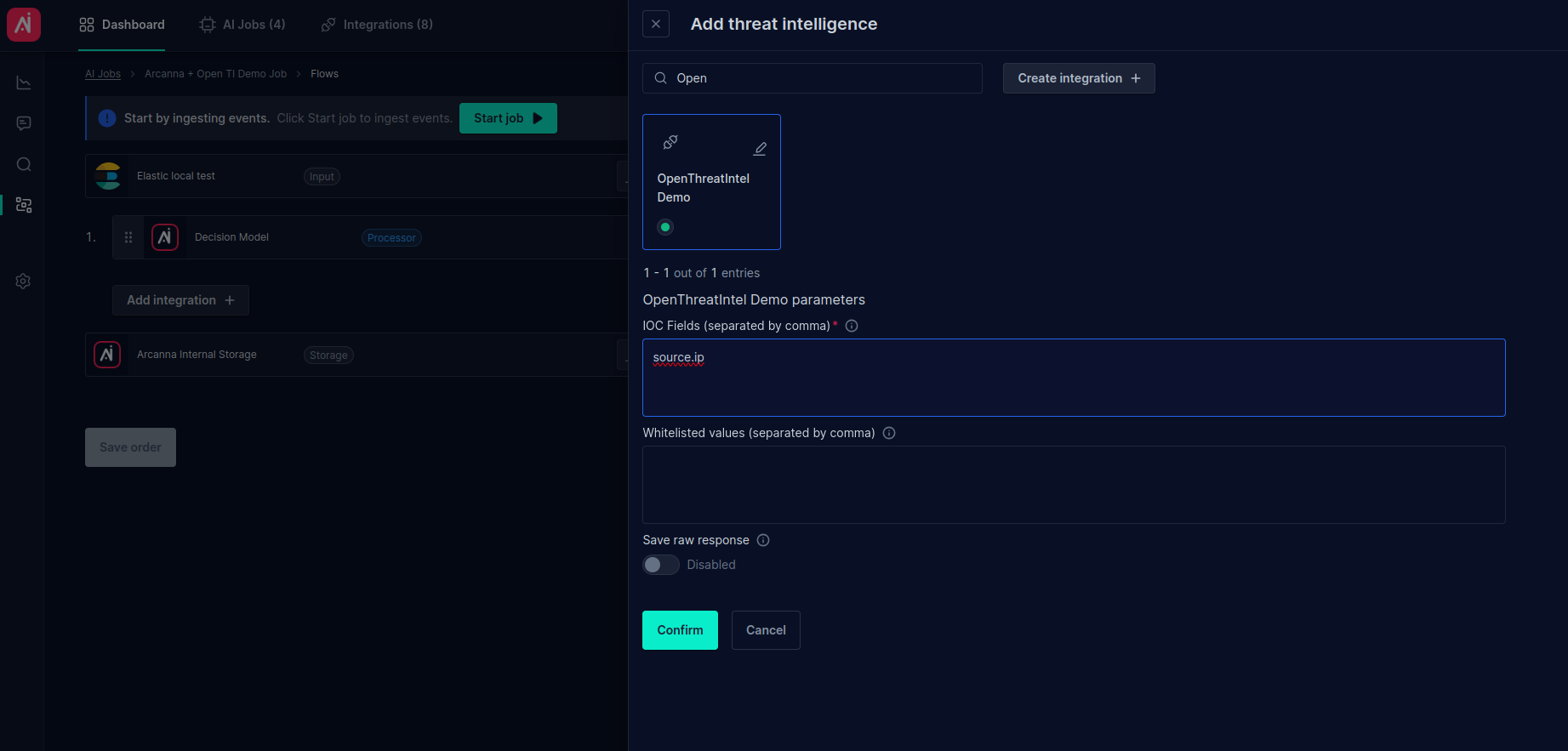
- Expand the Threat intelligence section and click Add +
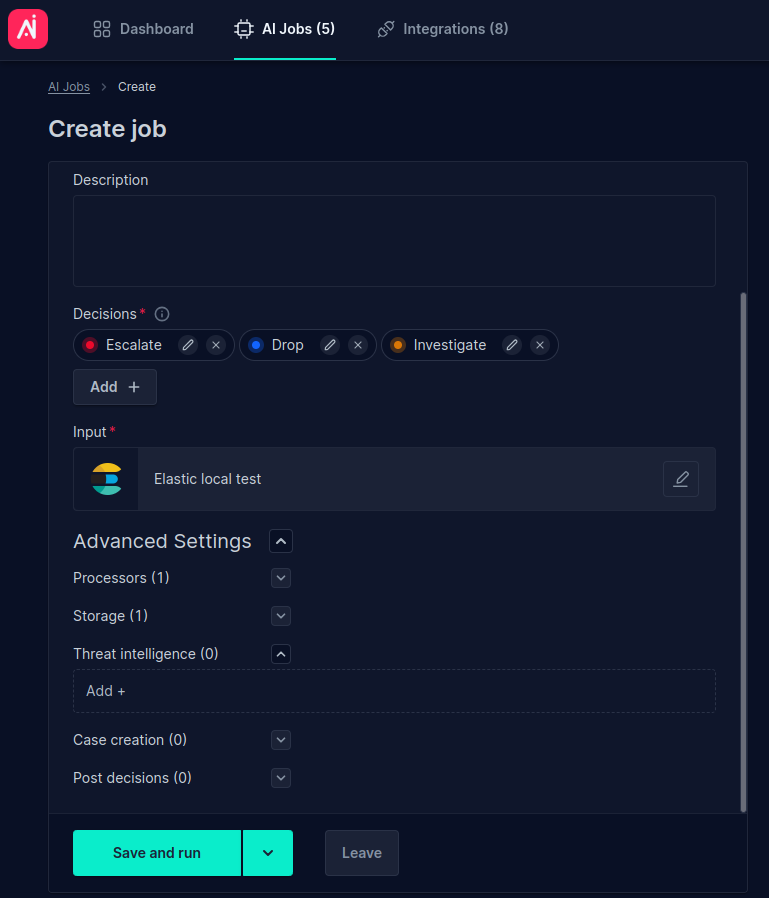
- Search for the Open Threat Intelligence integration. For testing, we are using
source.ipfield present in our input index. This field contains an IP address.
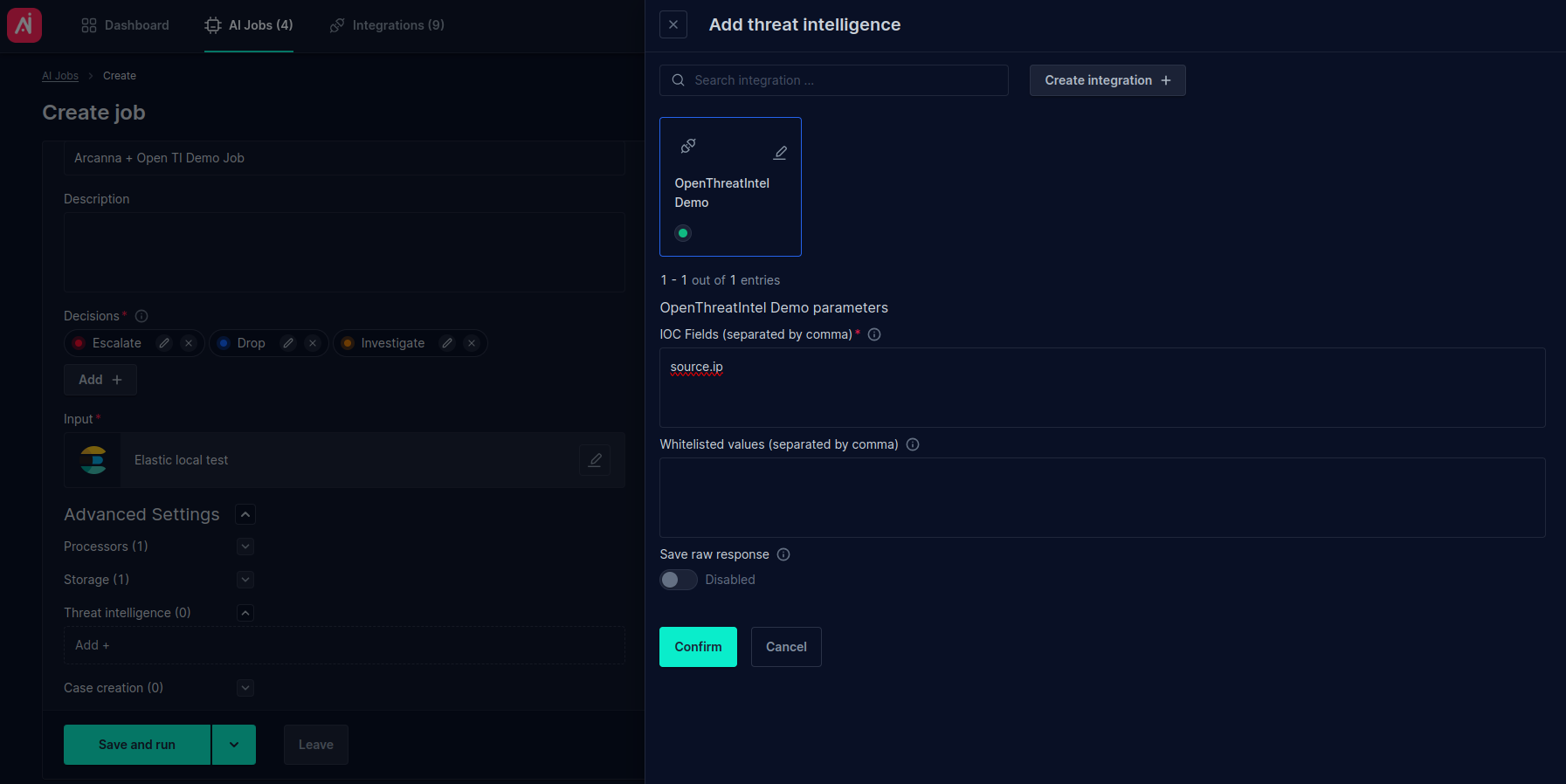
- Click Save and run to save and start the job
-
(Alternative) Add and configure the Open Threat Intelligence integration from the Flows page:
- Considering we already have an AI Use Case created, click on Flows
- Now on the Flows page click Add integration +, select Threat Intelligence from the popup.
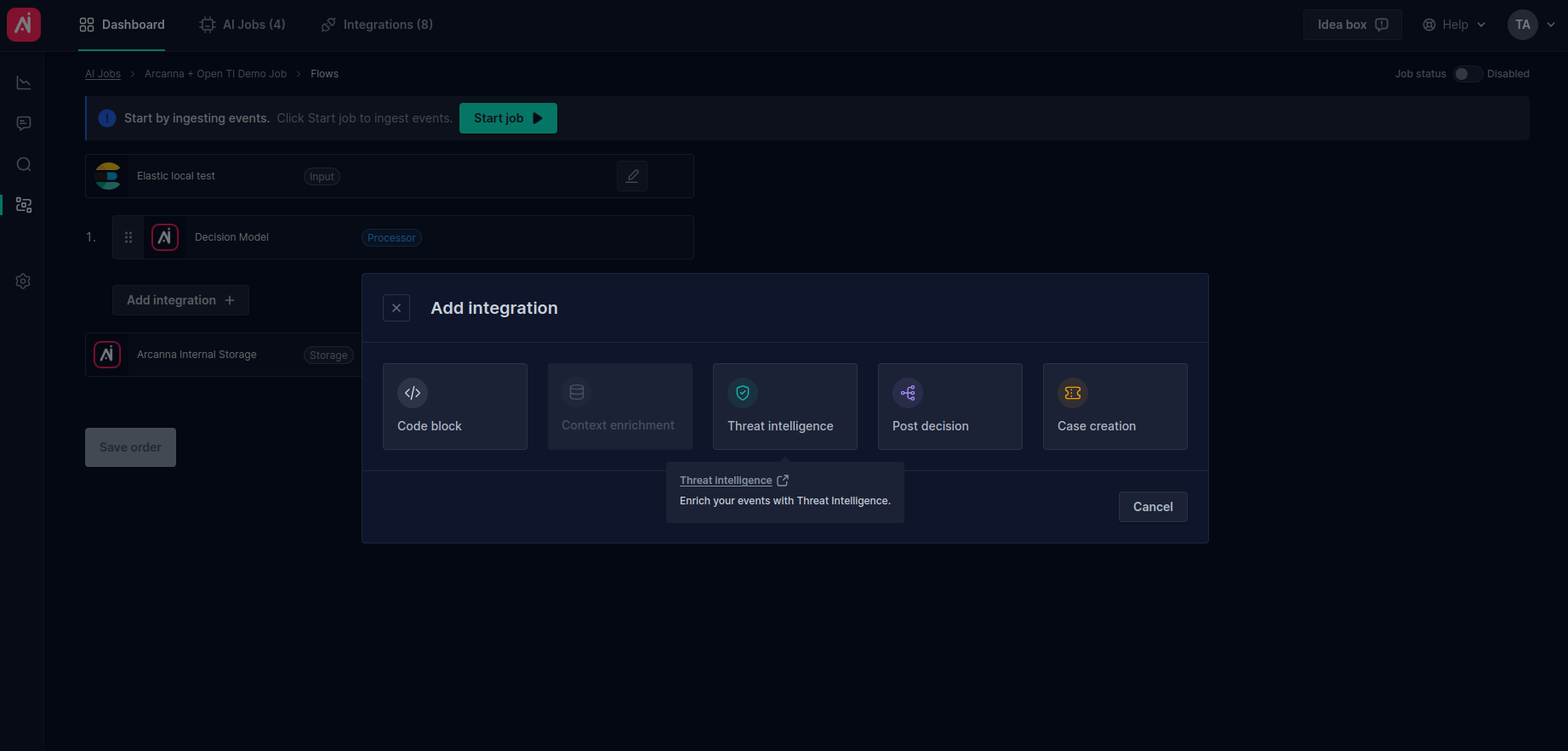
- Search for your Open Threat intelligence integration and type the IOCs fields to be investigated (e.g.: source.ip)
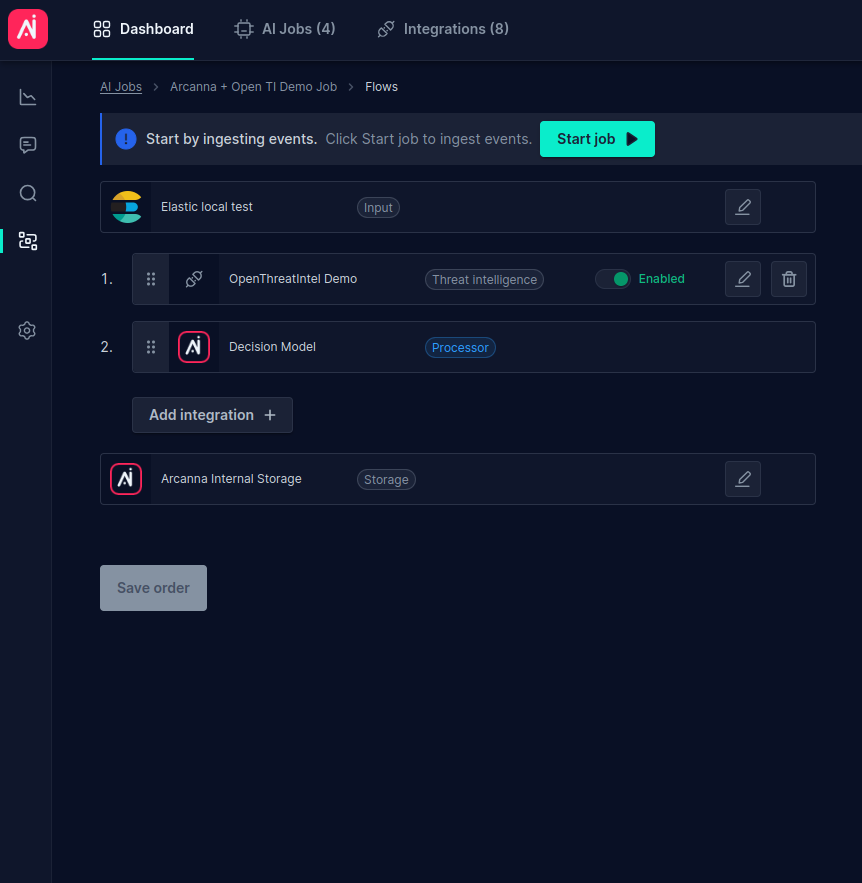
- From the Flows page, it is easier to observe the pipeline order. You can notice the threat intelligence steps are executed before the AI decision (processor). Also, the integration can be
Enabled/Disabledwithout losing the existing configuration.
-
Testing the Open Threat Intelligence enrichment
- Start the job (if not already started) by clicking Start job
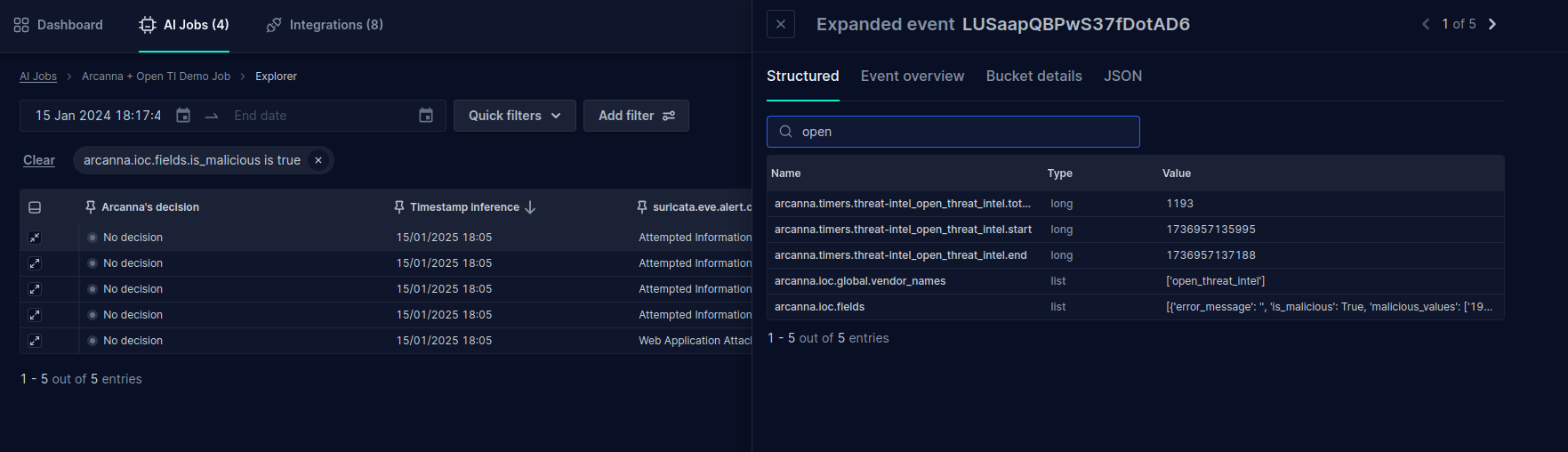
- Go to the job's Event Explorer page. Expand the event and go to the Event Overview tab. We can observe the threat intelligence step and its result. It the example shown above, we are inspecting an event marked with a malicious response.
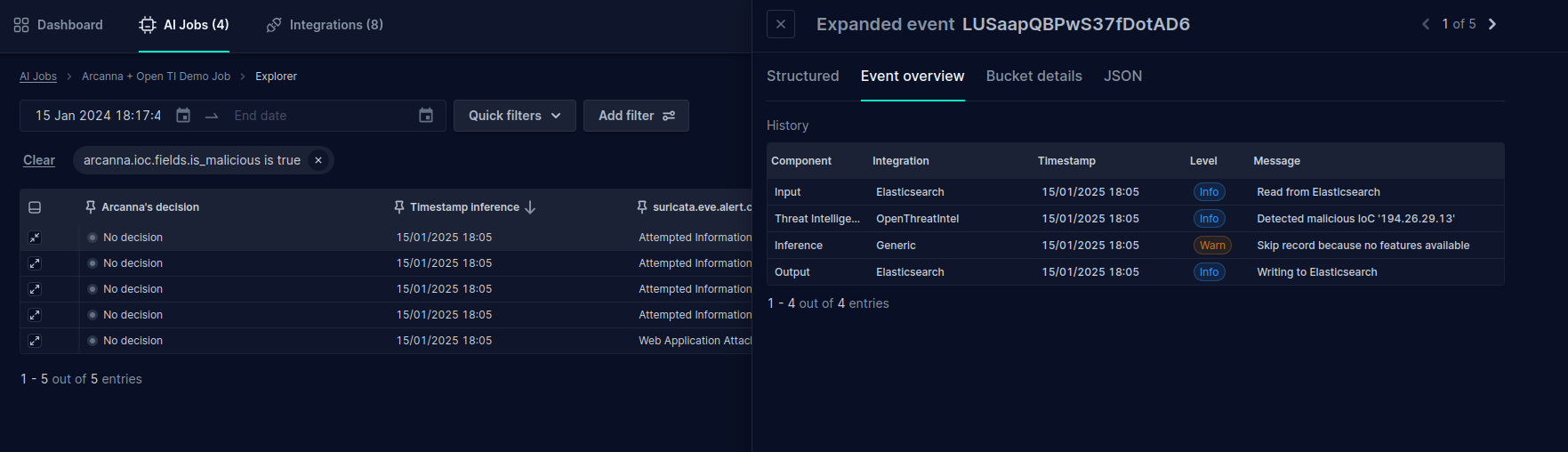
- Change to the Structured tab. We can observe the fields added to the event by the Open Threat Intelligence integration. Observe the general
is_maliciousflag is True.