VirusTotal
VirusTotal is a comprehensive platform for analyzing files, URLs, domains, and IP addresses to detect malicious content using multiple antivirus engines and URL scanning tools. It empowers security teams with real-time threat intelligence and detailed analysis, enhancing their ability to identify and respond to emerging cyber threats efficiently.
Arcanna - VirusTotal Integration
By integrating with VirusTotal, Arcanna enriches security events with comprehensive threat intelligence, enhancing the accuracy and speed of incident analysis and response.
Steps to configure VirusTotal integration:
Prerequisites
- A valid Arcanna.ai instance - for setup, follow this user guide.
- A valid VirusTotal account.
How to connect
Go to VirusTotal account:
- Select API key tab from the top-right menu:
- Copy API key to the clipboard for further used in Arcanna:
Go to Arcanna instance:
-
Create the VirusTotal integration:
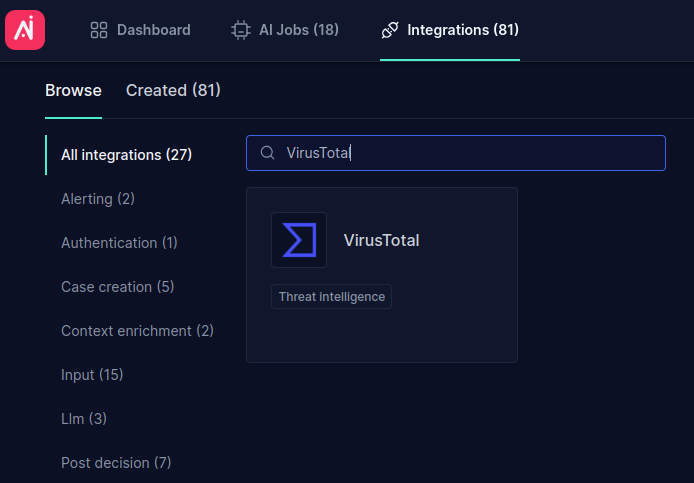
- Go to the Integrations tab
- Search for the VirusTotal integration and click on it:
- Fill in all the fields as shown below, using your own API Key and Title, then click Confirm:
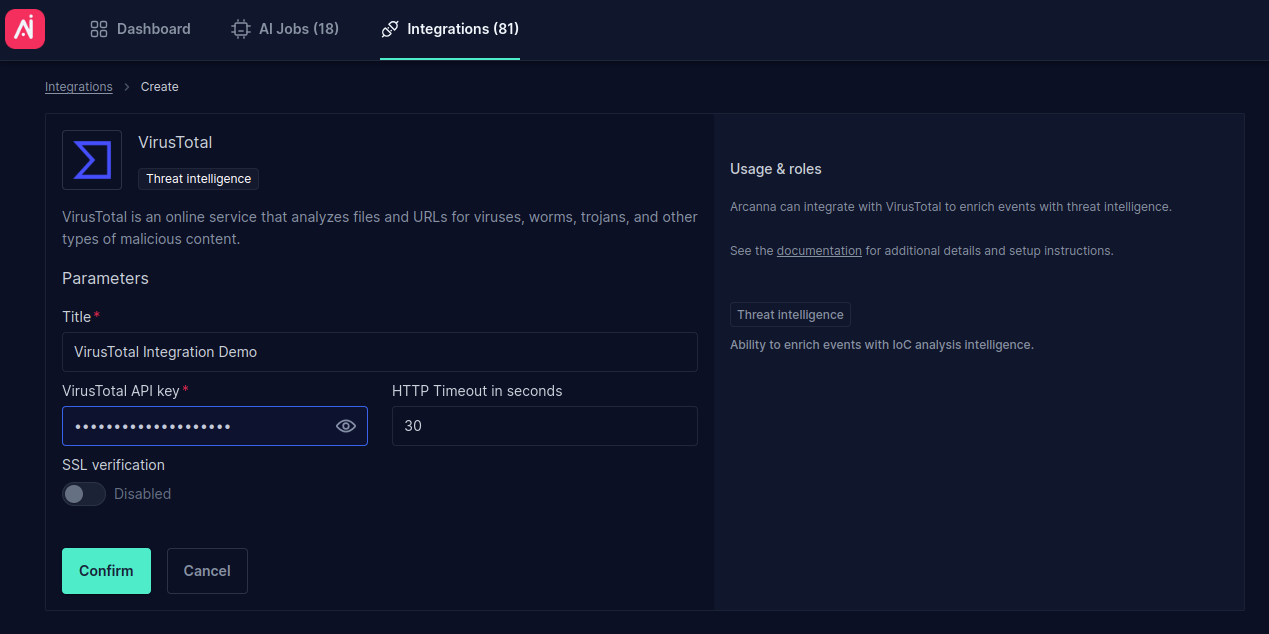
- If using both VirusTotal and Open Threat Intelligence, you can enable the option to bypass VirusTotal to reduce VT quota usage.
- Arcanna features a caching mechanism designed to optimize quota usage. The cache supports up to 10,000 fields or a retention period of 7 days, whichever is reached first.
-
Create an Arcanna job using VirusTotal integration:
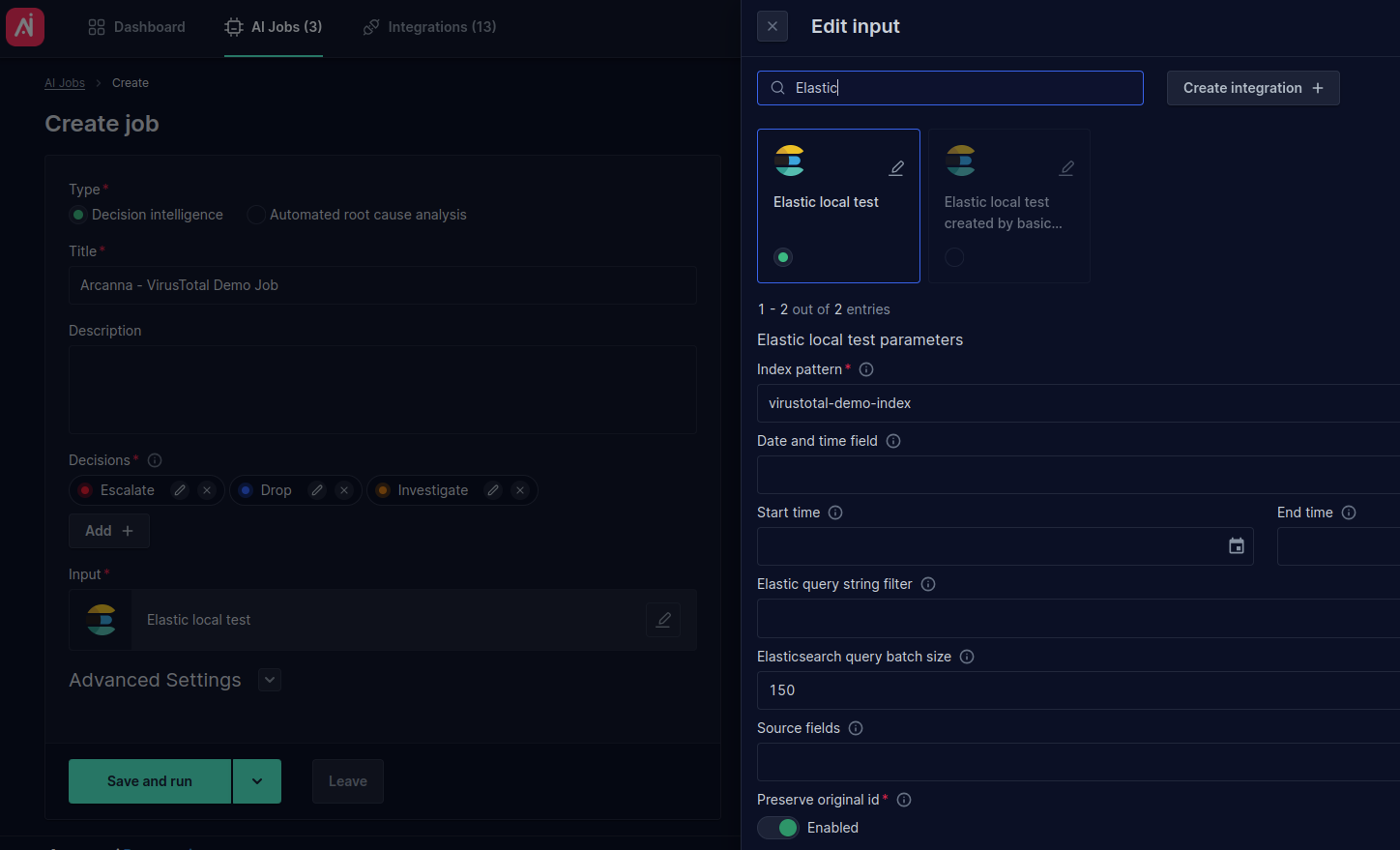
- Go to AI Use Cases tab and click Create Use Case:
- Complete the Title and select an input integration. For testing purposes, we used the Elasticsearch input integration with a test index named
virustotal-demo-index:
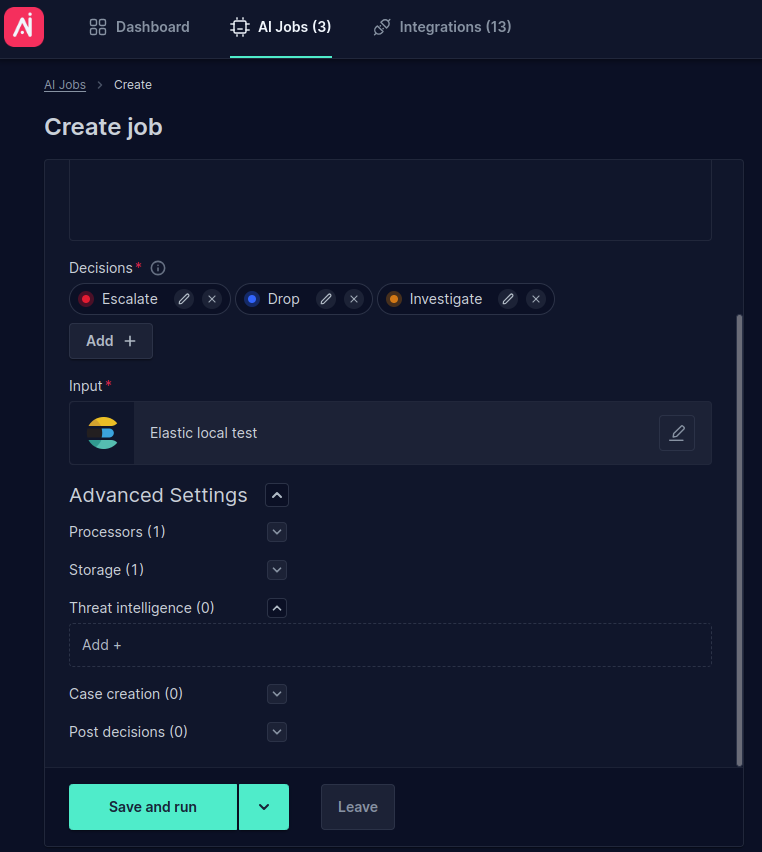
- Expand Threat intelligence tab and click Add +:
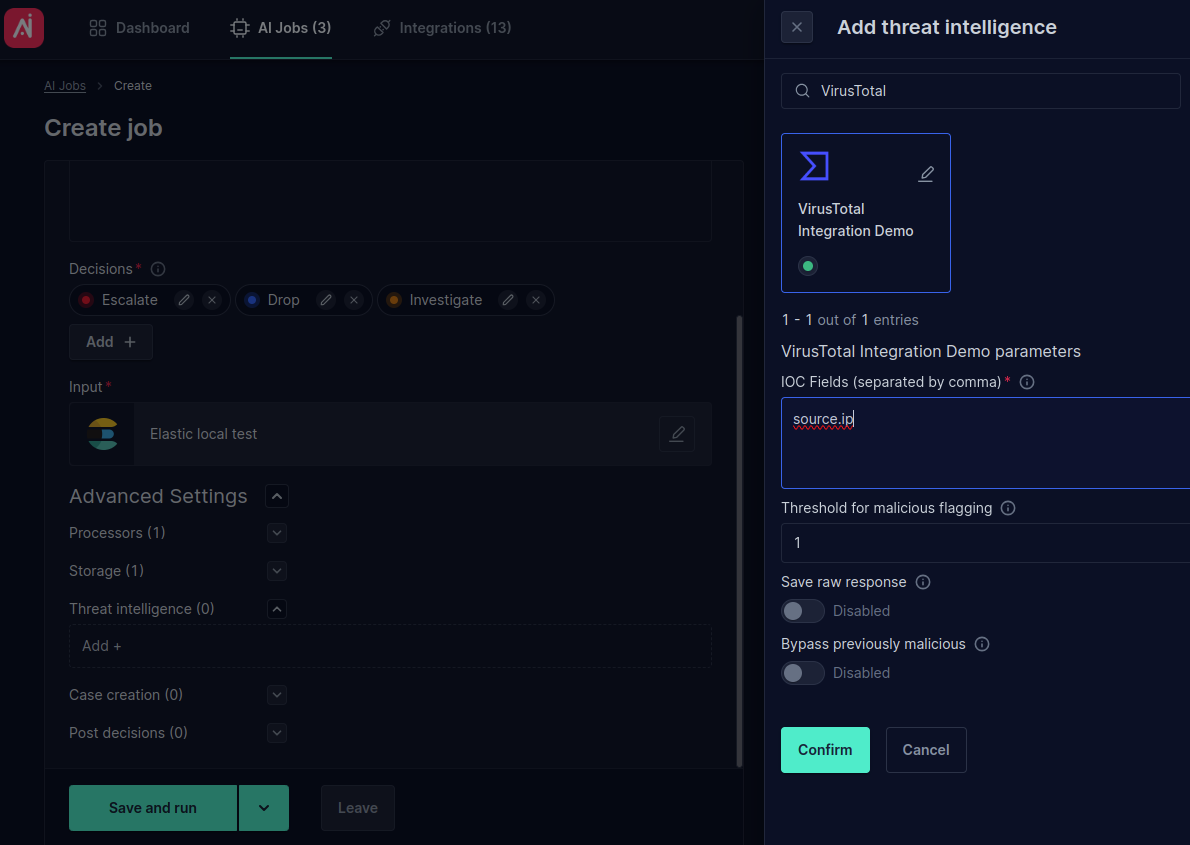
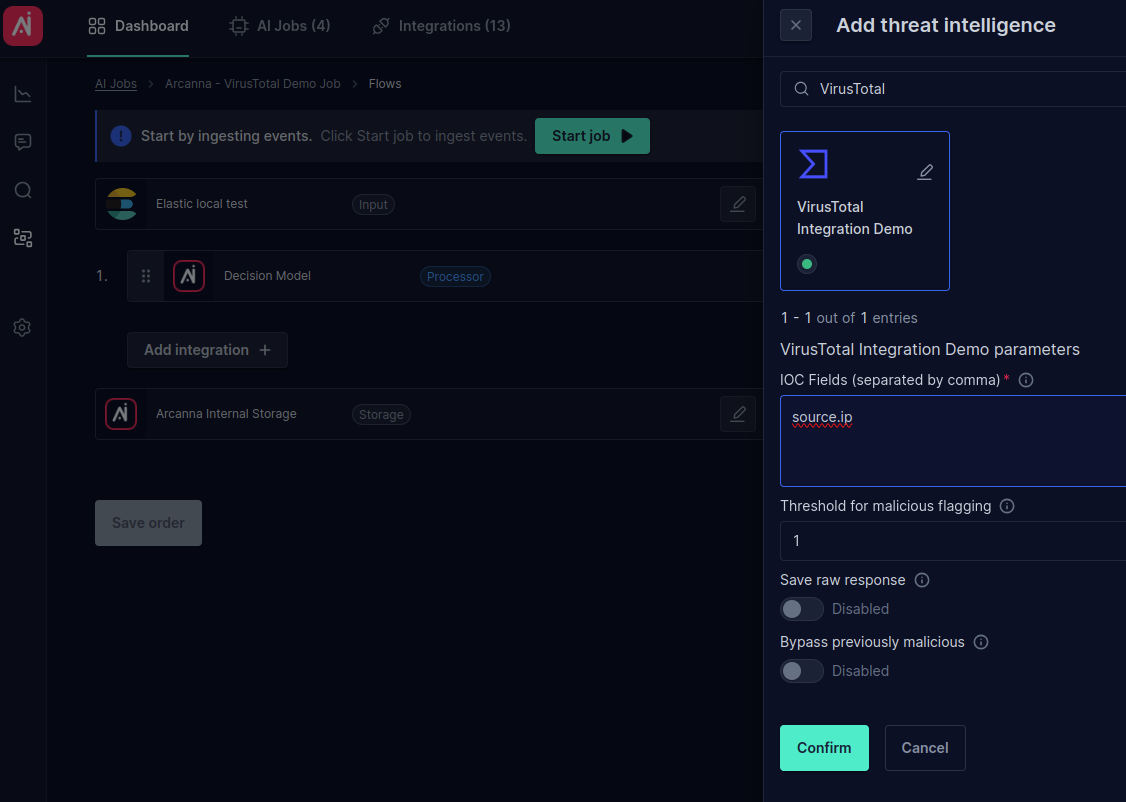
- Search for VirusTotal integration. For testing, we use the IOC field
source.ipfrom our test document:
- Click Save and run to save and start the job.
-
(Option 2) Add and configure VirusTotal integration from Flows page:
- Assuming an AI Use Case has already been created, click on Flows:
- On the Flows page, click Add integration +, search for VirusTotal, and select the IOCs to be investigated:
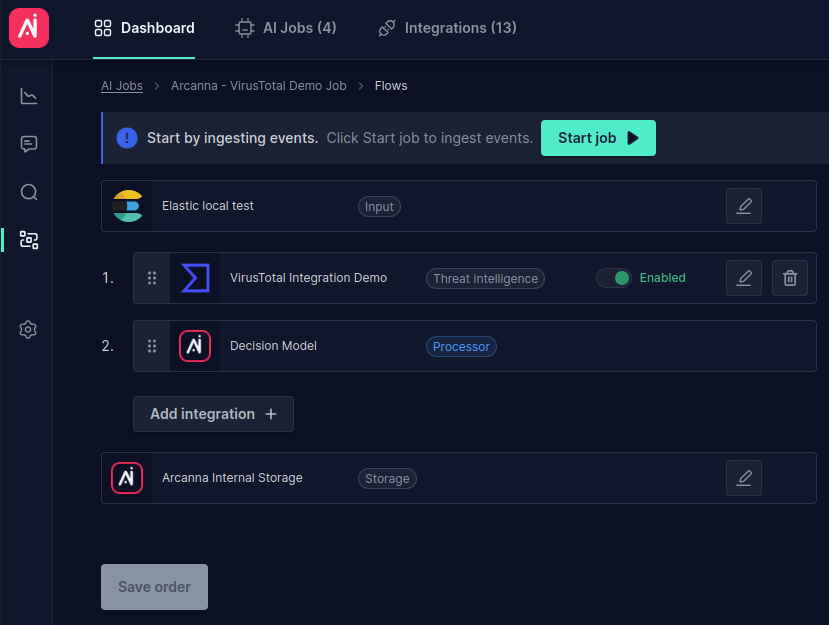
- From the Flows page, it is easier to observe the pipeline order of integration (e.g., threat intelligence preceding the AI Decision model). Additionally, the integration can be
Enabled/Disabledas desired:
-
Testing VirusTotal enrichment:
- Start the job by clicking Start job
- Go to the job's Event Explorer page. Expand the event and navigate to the Event Overview tab. Here, you can observe the threat intelligence and its result (e.g., the specific
source.ipflagged as malicious):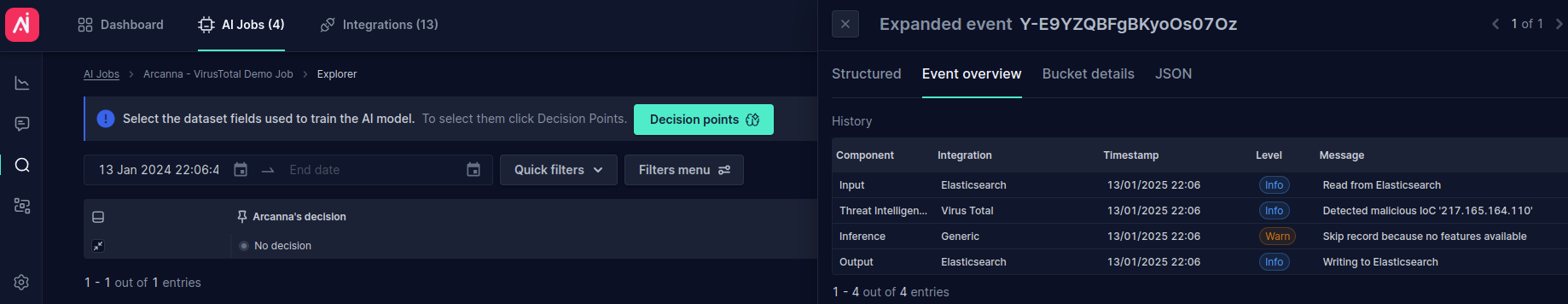
- Switch to the Structured tab. Here, you can observe the fields added to the event by the VirusTotal integration. Note that the general
is_maliciousflag is set to True: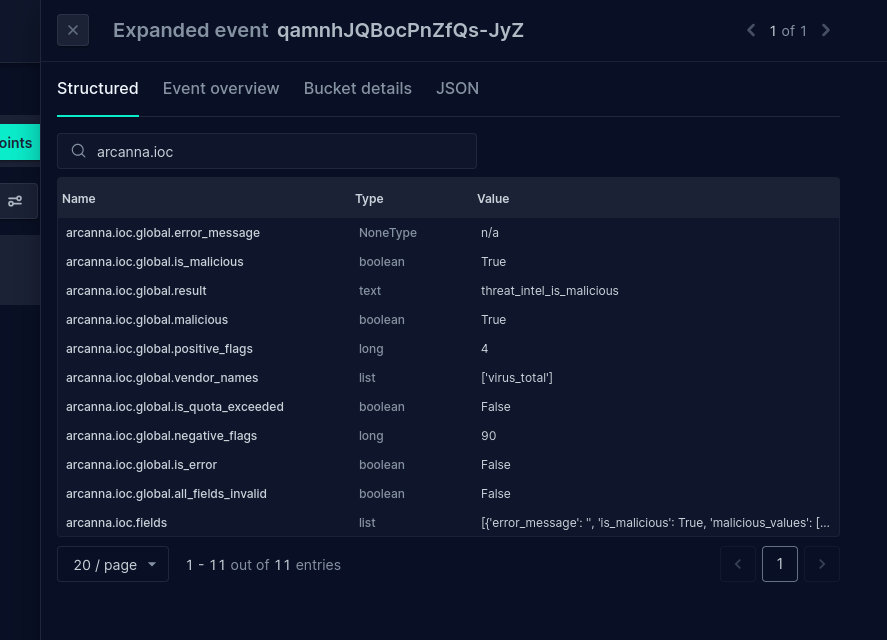
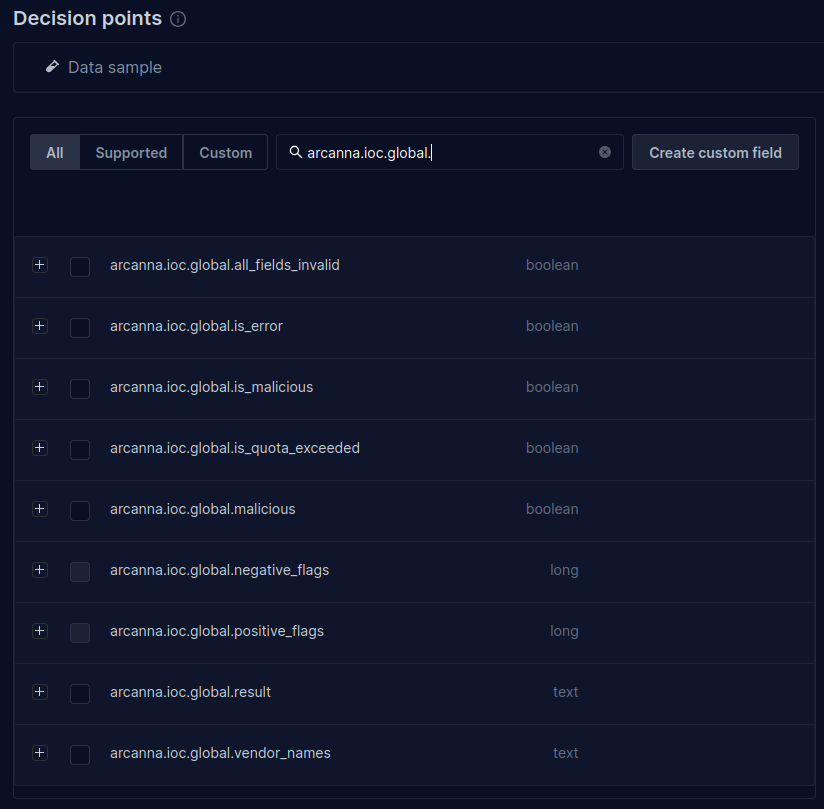
- Go to the Decision Points page. Here, the added fields can be selected for use as features in the Arcanna AI model. Typically, the field of interest is
arcanna.ioc.global.result, which contains the overall malicious result.